Assets, Issues, Compliance: We help you see in the dark.
Get Your Free Security Assessment
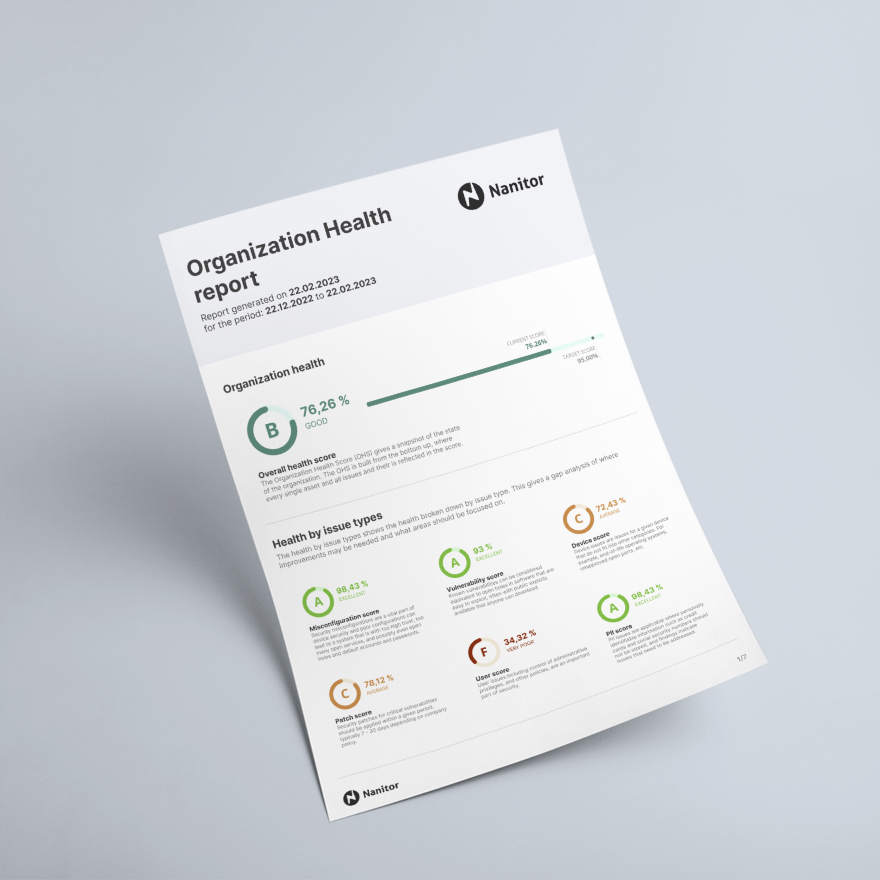
Book your consultation meeting with one of our in-house cybersecurity technical gurus to uncover the health score and security of your entire IT infrastructure. You'll receive a comprehensive report from our team via email at absolutely no cost whatsoever.
So, what are you waiting for?
By 2025, 70% of midsized companies will have been breached by a known vulnerability
Given the rapid ongoing growth of vulnerabilities, it has never been more paramount to take care of your IT infrastructure through an effective vulnerability management program.
Without this, you could be at risk of the following:
- Loss of revenue
- Downtime risk
- Failure to meet compliance regulations
How We Can Help?
Through the use of our market-leading vulnerability management system, we will qualify your company and walk you through setting up a free Nanitor agent on your systems. Our in-house experts will then take the wheel by quickly conducting a full and comprehensive audit of the entire IT infrastructure free of charge.
Our reports will showcase:
- Your Cybersecurity Health Score
- An Overview of All Known Vulnerabilities Across Your Systems and Devices
- A Prioritized List of Remediation Actions
What is Nanitor?
Nanitor is a powerful vulnerability management solution focusing on hardening security fundamentals across your global IT infrastructure. The platform provides unique visibility and control of your security challenges that stakeholders can trust, at a fraction of the cost and time of alternatives.

Why use the Nanitor platform?
Take a tour
Sign up now to gain instant access to take a tour of the Nanitor system – an enterprise-grade continuous threat exposure management CTEM solution for SMB's. Inside, our intuitive platform stands ready to guide you through each step with inbuilt tool-tips.

Our Interactive Nanitor Demo
Explore Nanitor's continuous threat exposure management (CTEM) Platform through our engaging interactive demo. Delve beyond conventional vulnerability management with advanced features like real-time threat detection, smart risk assessment, and customized security solutions. Embark on a transformative journey in cyber defense – start your immersive experience now.
What our customers say
Nanitor solution components
At the core of the system are 3 fundamental security components (Security Configuration, Vulnerability Management, and Patch Monitoring), collecting accurate real-time information from all your systems, visualized and prioritized in the Nanitor Diamond™.
components
components
components
components
Businesses must be able to protect their operations and data and ensure compliance
Whether you are working within fintech, travel, utilities, banking, municipalities, or engineering consultancy, operations and data management are integral to your business. Data leakage and loss of data integrity can occur from devices that are configured incorrectly or from attackers exploiting vulnerabilities. Knowing where these weaknesses are and remediating them will protect the data your business is handling. Across some verticals, regulation requirements are also essential, especially when working or expanding into different markets. Effective monitoring, management, and remediation of vulnerabilities is paramount to running a business.

Did we mention it's free?
Simply sign up for your consultation meeting with one of cybersecurity technical specialists below, and we'll take care of the rest.
Key benefits
01
Holistic view of the infrastructure
Nanitor provides an overview of all devices, software, users, configurations, known vulnerabilities, and missing security patches matched against PCI-DSS requirements. The outcome is a prioritized task list across your whole infrastructure that makes your remediation systematic and enjoyable.
02
Risk-based prioritization
Make the most of your limited resources by prioritizing the highest-risk issues. Nanitor assesses the risk of discovered issues based on external sources and assigns a prioritization score based on the asset criticality.
03
Blast radius minimization
Reduce the risk of lateral movement by hardening relevant configurations and known vulnerabilities. The best practice benchmarks for security configurations and known vulnerability databases are included in the platform.
04
Automatic monitoring
Nanitor automatically (in 5-minute intervals) checks and reports on thousands of compliance-related security issues across your infrastructure. Trust is good, verification is better.
Sign up for your free security assessment
How it works:
- Book your consultation meeting
- Complete the qualification questions (during the meeting)
- We complete the audit
- You receive the report






