Cybersecurity
What is CTEM? A Non-Technical Guide to Continuous Threat Exposure Management

22.07.25
4 min read
Why Cyber Risk Feels Overwhelming Today
In boardrooms and executive meetings across the world, the same fear is echoing louder than ever: Are we really protected against a cyberattack?
It’s a valid concern—and a growing one. Modern digital infrastructure is more complex than ever. You’re dealing with remote workers, hybrid cloud environments, third-party vendors, and sprawling software stacks. Everything is connected, and every connection is a potential risk.
Cyberattacks are no longer rare or abstract. They’re hitting manufacturers, hospitals, law firms, logistics providers—businesses just like yours. The cost of a breach? Millions in damage, loss of trust, and operational disruption. For many executives, it's not just about compliance anymore—it’s about survival. And here's the hardest part: Traditional cybersecurity approaches are falling short.
You might already be investing heavily in firewalls, antivirus tools, and periodic audits. But despite all this, the fear remains. Most leaders simply don’t have a clear answer to the question: Where are we exposed, and what should we fix first?
That’s where CTEM—Continuous Threat Exposure Management—comes in. It’s a smarter, ongoing approach that brings visibility, control, and peace of mind to today’s chaotic threat landscape.
What Is CTEM? (Continuous Threat Exposure Management)
Let’s start with a simple definition: CTEM is a continuous, structured approach to identifying, assessing, and mitigating your organization’s real cybersecurity risks in real-time.
It’s not a single tool. It’s not another checkbox. CTEM is a strategic shift that gives leaders ongoing visibility into what truly matters—and the confidence to act on it. What the name means:
- Continuous: Not once a year. Not even once a quarter. CTEM runs all the time.
- Threat Exposure: This is the full range of cybersecurity risks and vulnerabilities a company faces. CTEM doesn’t just flag vulnerabilities—it shows you which paths an attacker could take, and which assets are truly at risk.
- Management: CTEM gives you clear, prioritized, measurable actions—not just raw data or endless alerts.
In other words, CTEM is about clarity, not complexity. It helps leadership teams understand cyber risk the same way they understand financial or operational risk.
CTEM helps you continuously understand what threats matter most, where you’re exposed, and what to fix next — so attackers have fewer chances to win.
Why CTEM Came About
CTEM didn’t emerge by accident. It was born out of frustration—and necessity. What wasn’t working:
- Traditional security models: These rely on firewalls, annual audits, long checklists, and assumptions that don’t reflect the current pace of threats.
- Alert fatigue: IT and security teams are buried under notifications, but can’t see what’s actually dangerous.
- Ransomware and supply chain attacks: Threats have grown more sophisticated, targeting not just systems but humans, vendors, and overlooked entry points.
- Regulatory pressure: Laws like NIS2, ISO 27001, and DORA now require organizations to demonstrate proactive, ongoing risk management.
- Disconnected leadership: Boards want answers. CISOs and IT teams want clarity. But the language and priorities are often misaligned.
CTEM changes that: It bridges the gap between technical risk and business reality—giving executives a view of cyber exposure that aligns with what they care about most: impact, probability, and cost.
“By 2026, organizations prioritizing their security investments based on a continuous exposure management programme will be three times less likely to suffer from a breach.”
- Gartner
What CTEM Looks Like in Practice
So how does Continuous Threat Exposure Management actually work? A modern CTEM platform delivers these capabilities:
- Real-Time Visibility: CTEM continuously scans and maps your IT environment—automatically discovering every device, server, application, and cloud asset. No more blind spots.
- Risk Based on Attack Paths: Not every vulnerability is dangerous. CTEM shows how attackers could move through your environment—identifying real threats based on how systems connect and how damage could spread.
- Clear Executive Reports: Instead of overwhelming technical details, CTEM platforms translate exposure into business impact. You get dashboards that show risk by department, location, or asset value.
- Ongoing Updates: Annual audits are too late. CTEM refreshes continuously—so your data reflects your current reality, not last quarter’s guesswork.
- AI-Driven and Scalable: Modern CTEM solutions like Nanitor use automation and AI to reduce noise, cut down manual work, and scale without needing a larger security team.
Importantly, CTEM isn’t another tool to add to the pile. It’s a shift in how your organization approaches cyber risk—from reactive firefighting to proactive management.
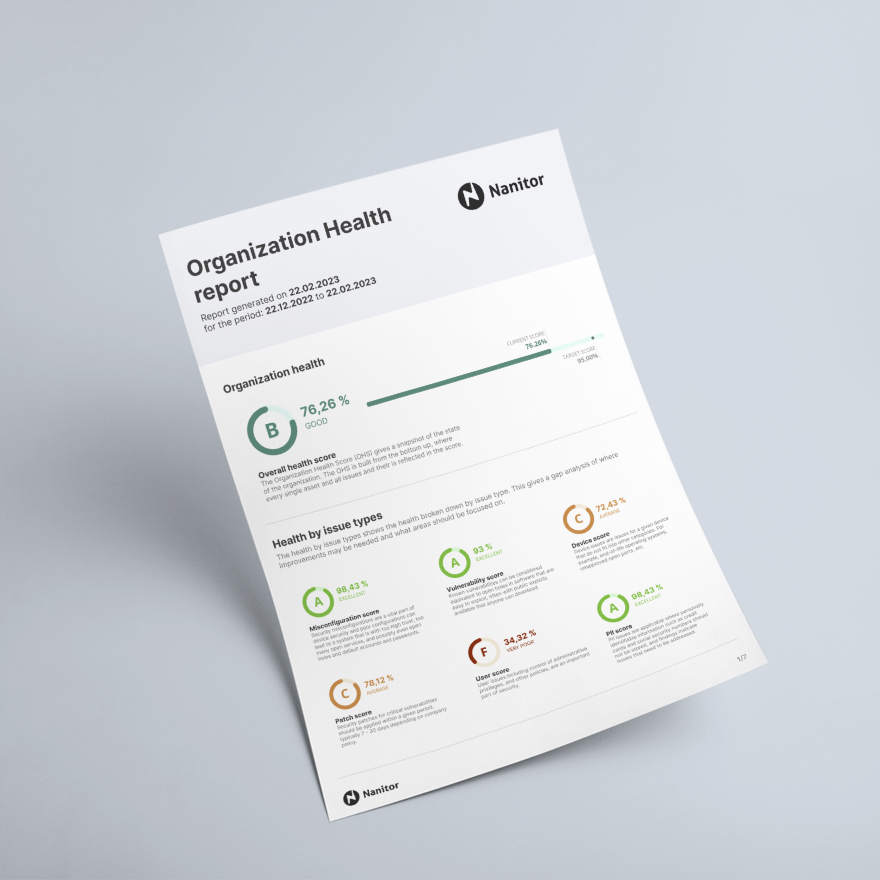
Key Business Benefits of CTEM - CTEM delivers more than just IT improvements—it creates real business value.
01
Understand Cyber Risk in Business Terms
Boards don’t want to know how many patches are missing. They want to know: What’s at risk? What’s the cost? What should we fix first? CTEM makes those answers available.
02
Prioritize What Actually Matters
Stop trying to fix everything. CTEM ranks exposures by real-world impact, so your teams focus only on what reduces risk now.
03
Align IT, Security, and Business Goals
With CTEM, technical teams and leadership use the same language and the same data—making collaboration easier and more effective.
04
Simplify Compliance
Frameworks like NIS2 require you to prove that you’re managing risk continuously. CTEM platforms generate evidence and reports that make audits simpler and faster.
05
Make Cybersecurity Measurable
With CTEM, cybersecurity isn’t vague or reactive—it’s a measurable, manageable part of your business strategy.
Final Takeaway: CTEM Is Cybersecurity for Business Leaders
Cybersecurity doesn’t need to be a black box. With Continuous Threat Exposure Management, you gain clarity, not confusion. You know what your risks are, where you’re vulnerable, and how to reduce exposure in a way that aligns with your business goals. And most importantly—you can sleep better at night. You know you’re not waiting for the next attack. You’re actively managing your risk, continuously, and with confidence.
CTEM is not just a trend. It’s the new standard for how smart organizations approach cybersecurity. It gives you a financial audit-level view into your digital risks—updated in real time, prioritized by impact, and tailored for leadership.
Want to Learn More?
If you're exploring how CTEM can help your organization take back control of cybersecurity risk, Nanitor can help. As pioneers in clarity-first CTEM, Nanitor helps businesses of all sizes gain real-time visibility and make cybersecurity actionable.